Microsoft Teams Admins can no longer create Teams Phone Resource Accounts

Less than a month ago (Apr 18, 2024), Microsoft announced via Message Center (MC780743) that the following Entra roles:
- Teams Administrator
- Teams Communications Administrator
- Teams Telephony Administrator
Will no longer grant the ability to create Resource Accounts.
Starting in mid-July 2024, only Global Administrators or User Administrators can create and manage Resource accounts.
This change is significant in several organizations where Teams and Telephony administrators require the ability to set up resource accounts to build their Auto Attendants or Call Queues.
Bring on the standoff between Entra Admins trying to enforce the principle of least privilege and Teams/Telephony Admins needing to create resource accounts.
Why is Microsoft Changing Roles required to create Teams Resource Accounts?
After a series of high-profile cyberattacks, it really seems Microsoft is overhauling its security processes. Earlier this month, Microsoft CEO Satya Nadella made it clear through a memo to Microsoft’s over 200K employees that security should be prioritized above all else.
If you’re faced with the tradeoff between security and another priority, your answer is clear: Do security. In some cases, this will mean prioritizing security above other things we do, such as releasing new features or providing ongoing support for legacy systems. This is key to advancing both our platform quality and capability such that we can protect the digital estates of our customers and build a safer world for all.
I have a strong suspicion that the recent changes regarding Resource Accounts result from Microsoft's security team following the new guidelines published by Nadella. The change makes mention of discontinuing the use of an underlying service permission and instead using the Microsoft 365 admin role's permission to create user accounts.
How can your Organization Prepare?
It’s time to assess the process your Teams Voice Administrators use to create Resource Accounts and validate who should have the necessary permissions to create and manage Microsoft 365 users.
If you’re considering assigning the user administrator roles to your team admins, there are a few things to consider and recommended ways to do so.
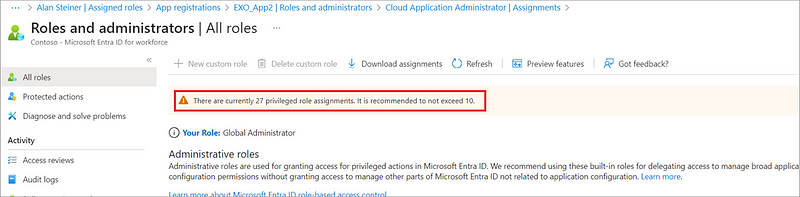
The Global Admin and User Admin Roles are both privileged roles, meaning that they can be used to delegate management of directory resources to other users, modify credentials, authentication or authorization policies, or access restricted data.
In short, privileged role assignments can lead to elevation, so granting them to users is a significant responsibility that requires extra care. Microsoft’s best practices recommend limiting privileges to fewer than 10 people in your organization.
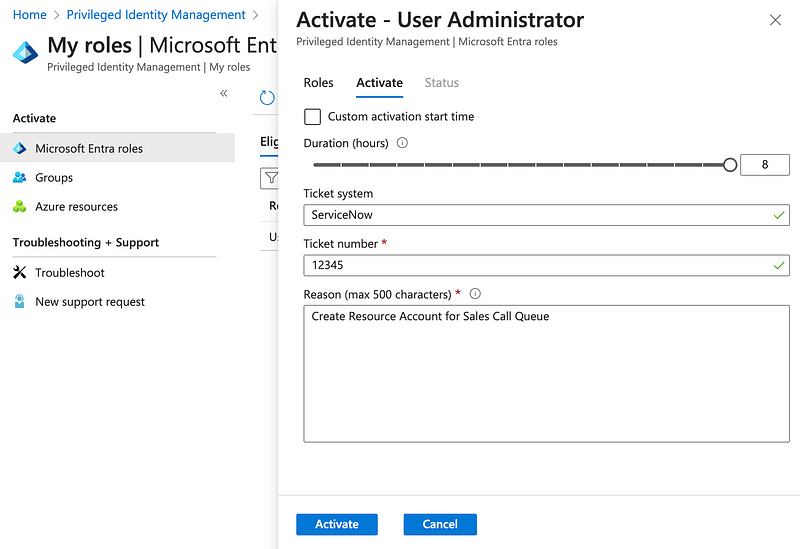
Using Privileged Identity Management (PIM) with Just in Time Access
With just-in-time access in PIM, your Global Administrator or Privileged Role Administrator could provide some of your Microsoft Teams admins with an eligible assignment.
Eligible assignments provide temporary access and optionally require the requestor to provide additional information with their request such as providing a business justification or requesting approval from designated approvers before the role is granted.
For more information, see Configure Microsoft Entra role settings in Privileged Identity Management.
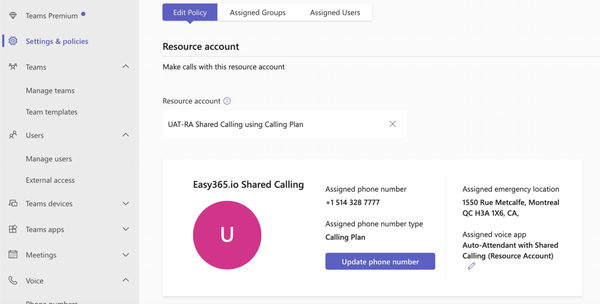
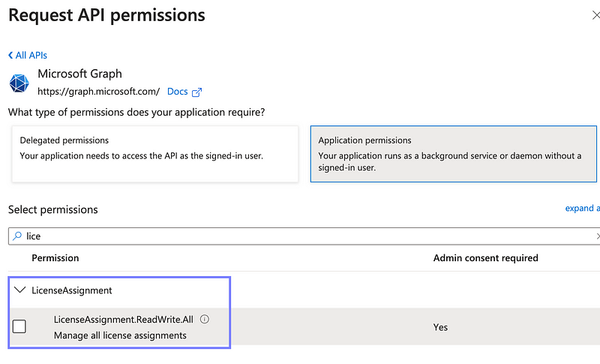
Automating Teams Phone Resource Account Creation with APIs?
Scripters/ app builders such as myself who are creating mass buildouts of Call Queues or Auto Attendants cannot leverage app-based authentication against the Teams Powershell Module or Graph to create Resource accounts.
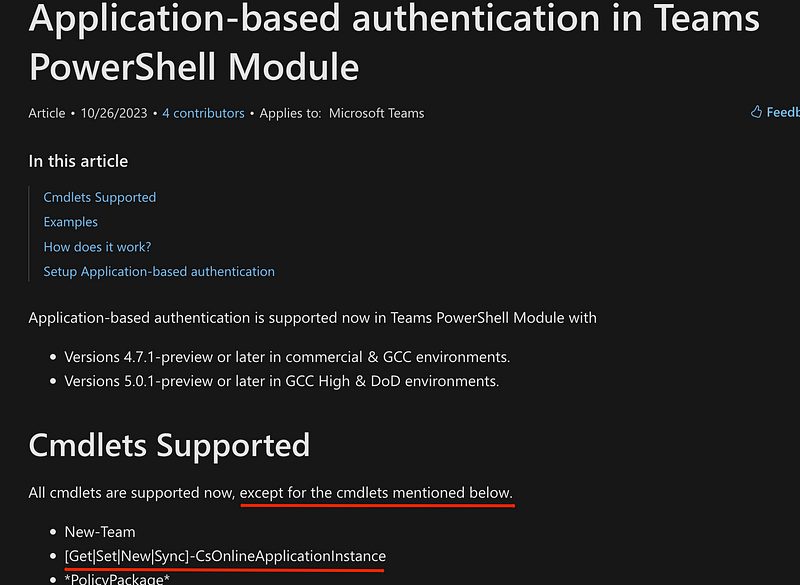
The command New-CsOnlineApplicationInstance sadly, requires an interactive login with a user account, which will likely require the additional User Administrator Role or Global Admin Role.
I eagerly await the day when the Teams Powershell Module, the Graph API or even the underlying APIs (https://api.interfaces.records.teams.microsoft.com/Teams.PlatformService/ApplicationInstances) permit the creation of Teams Phone Resource Accounts with a Graph Role and app-based auth.
You have a few options
In short, it seems like this change will require team administrators to re-evaluate their approach to creating Call Queues and Auto Attendants. The available options include:
- Teams Admins to request a resource account from a User Admin or Global Admin when creating new Auto Attendants or Call Queues
- Grant the additional roles to Teams Admins using Privileged Identity Management (PIM) with Just in Time Access
- Create a pool of Resource Accounts that are on “standby” and ready to be assigned. (Shout out to Martin Heusser | M365 Apps & Services MVP who shared that idea with me)
Did I miss any other potential options/ideas? Drop me a comment! 😊